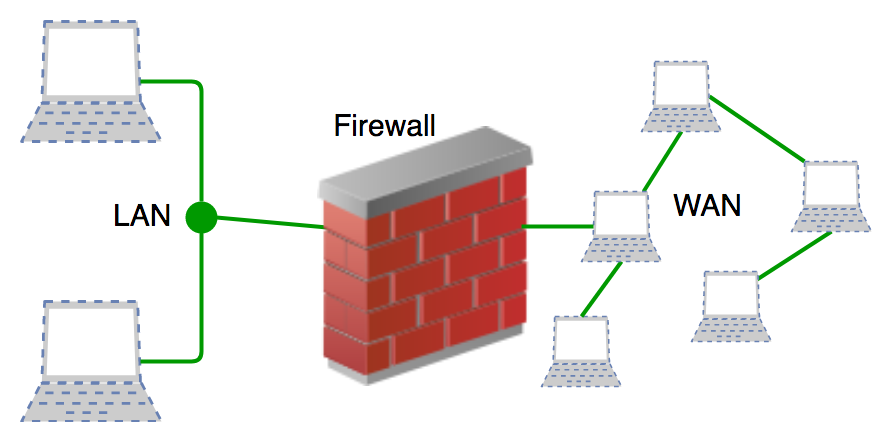
A firewall provides a security tool that guards your network against unauthorized access to confidential information. Stormshield protects the systems against harmful malware. Firewalls separate trusted internal networks from unauthorized external networks.
Depending on the security requirements of your customer, firewalls provide varying levels of protection. Firewalls have served as the initial line of defense in security systems for networks for a significant length of time. Learn more about the importance of firewalls in cyber security by reading on.
What function do firewalls serve in cybersecurity?
Firewalls monitor attempts by unauthorized traffic to enter the operating system of your client. Between systems and other networks, they create barriers.
Additionally, firewalls manage and verify your client’s network access as traffic controllers. Most computer operating systems as well as security programs come with a firewall already installed.
Managed service providers (MSPs) may simplify host-level protection by using firewalls to take the guesswork out of it. Malware and application-layer assaults will be prevented by firewalls with integrated intrusion prevention systems. Additionally, they detect assaults throughout your whole network and respond swiftly and flawlessly.
Web traffic management relies heavily on network security firewalls because they reduce the spread of online dangers.
Functioning of a firewall
The majority of the time, firewalls accept inbound connections that are authorized to access a network. Depending on the security rules in place, security measures will either let or block data packets. Web traffic is filtered by firewalls through checkpoints. Before the targeted network suffers any damage, these solutions let you examine and respond to errant network activity.
Only reputable IP addresses and sources are allowed to access your client’s systems when a reliable firewall is in place. Some firewalls can check audit logs for connections and throughput of traffic.
Use firewalls to secure the host devices’ and private networks’ perimeters. When establishing user access controls, make sure to use strong firewalls. On user PCs or dedicated computers connected to the network, you can install these barriers.
Firewalls’ importance in cybersecurity
Networks without security are frequently targets of assaults. It is beneficial to verify network traffic to see if it is hazardous or not. Users become susceptible to several possible hazards the moment they link their personal devices to computer networks or the internet. Network infiltration is a possibility when combining resources and streamlining online cooperation.
When users connect their gadgets to other networks, they frequently run the danger of identity theft, hacking, and online fraud. Cybercriminals on the loose might repeatedly threaten networks and devices. The likelihood of such network assaults rises with the accessibility of internet connections.
The conclusion
With the proactive protection provided by firewalls, you may browse the internet with increased security. They may be used to screen out a variety of possible risks on client networks.